The crooks behind the CryptoLocker malware seem to have introduced a second chance option.
Victims, it seems, can now change their minds about not paying up.
Assume you were a victim of this devious malware, and decided, “No! I will not pay!”
Imagine that you’ve done a full cleanup; removed the malware from memory, hard disk and Windows registry; and gone to see what you can recover from your backup disks.
Now imagine that you are having malware cleaner’s remorse.
Perhaps paying $300 would have been the pragmatic approach?
→ As we’ve been saying, our recommendation is not to pay up, but we also have to admit that it’s easy for people who haven’t had their favourite files scrambled to take that attitude.
Perhaps you had the malware for longer than you realised, and the backups you thought would help are scrambled?
Perhaps your infected computer had access to documents on a server at the office, and ruined other people’s files, too?
In short, perhaps you’d like a chance to change your mind?
Enter the CryptoLocker Decryption Service:
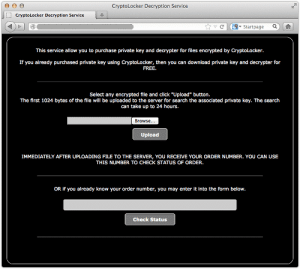
This service allow you to purchase private key and decrypter for files encrypted by CryptoLocker.If you already purchased private key using CryptoLocker, then you can download private key and decrypter for FREE.Select any encrypted file and click "Upload" button.The first 1024 bytes of the file will be uploaded to the server for search the associated private key. The search can take up to 24 hours.IMMEDIATELY AFTER UPLOADING FILE TO THE SERVER, YOU RECEIVE YOUR ORDER NUMBER. YOU CAN USE THIS NUMBER TO CHECK STATUS OF ORDER.OR if you already know your order number, you may enter it into the form below.
Apparently the crooks will now let you buy back your key even if you didn’t follow their original instructions.
Word on the street, however, is that the crooks want five times as much as they were charging originally to decrypt your data after you change your mind
The cost of is now 10 Bitcoins instead of the 2 Bitcoins they were after at the start – a sort of late payment penalty, like the taxation office imposes.
According to this latest website, you send them the first 1024 bytes of any encrypted file in order to determine your eligibilty for the new “service,” and then wait up to 24 hours.
We’re guessing that the delay is because the crooks have to run a brute force attack against themselves.
Without your public key to help them match up your keypair in their database, it sounds as though they have to try to decrypting your data with every stored private key until they hit one that produces a plausible result.
They’re not actually saying whether this new service works even if the 72 hour deadline imposed at the start has expired.
The implication, however, is that it will – not least because the 24-hour delay needed to process your “order” would otherwise reduce that deadline to 48 hours, cutting down their window for extortion substantially.
Furthermore, those 48 hours would have to include the time for you to clean up, find that you couldn’t recover by more palatable means than the initial threat, change your mind, and contact the “second chance” website.
If so, the crooks’ original claim was bogus all along:
The single copy of the private key, which will allow you to decrypt the files, located on a secret server on the Internet; the server will destroy the key after a time specified in this window. After that,nobody and never will be able to restore files.
Nobody and never, eh?
We’re still saying, “Don’t buy,” but we’re feeling your pain enough to know how tempting it will be for some people to pay the crooks, even though the blackmail charges have now ballooned to more than $2000.
In the meantime, if you’ve decided not to pay – or have escaped the depredations of these crooks so far – we urge you to check out our advice:
- Destructive malware “CryptoLocker” on the loose – here’s what to do
- CryptoLocker ransomware – see how it works, learn about prevention, cleanup and recovery
Via NakedSecurity

