Loziok trojan used to siphon confidential data out of infected computers.
Researchers have uncovered an ongoing espionage campaign that uses custom-developed malware to siphon confidential data out of energy companies around the world.
Trojan.Laziok, as the malware has been dubbed, acts as a reconnaissance tool that scours infected computers for data including machine name, installed software, RAM size, hard disk size, GPU details, CPU details, and installed antivirus software, according to a blog post published Monday by researchers from security firm Symantec. The attackers then use the data to decide how to infect the computer with additional malware, including versions of Backdoor.Cyberat and Trojan.Zbot that are tailored for a specific compromised computer.
“The detailed information enables the attacker to make crucial decisions about how to proceed further with the attack, or to halt the attack,” Symantec researcher Christian Tripputi wrote. “During the course of our research, we found that the majority of the targets were linked to the petroleum, gas and helium industries, suggesting that whoever is behind these attacks may have a strategic interest in the affairs of the companies affected.”
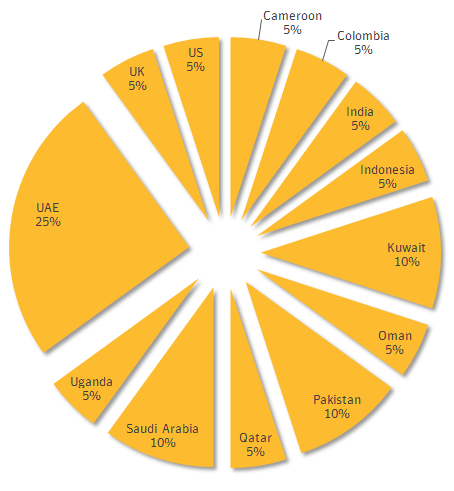
The United Arab Emirates was the country most targeted by the attackers, followed by Saudi Arabia, Pakistan, and Kuwait.
Computers are initially infected with Laziok through spam e-mails coming from the moneytrans[.]eu domain. The e-mails contain a malicious attachment that exploits a Microsoft Windows vulnerability that was patched in 2012. The same vulnerability has been exploited in other attack espionage campaigns, including one that used the Red October malware platformto infect diplomatic, governmental, and scientific organizations in at least 39 countries. The Laziok exploit typically came in the form of an Excel file.