Summary: Microsoft has had multi-factor authentication support for Office 365 administrative accounts since last year. Now that important security feature is available for ordinary user accounts in Midsize Business and Enterprise plans.
By Ed Bott for The Ed Bott Report
From a network administrator’s point of view, there’s almost nothing worse than a compromised corporate email account. An outsider who can successfully break into that account can wreak havoc with every device and service that’s connected to it, accessing whatever information that user has access to and using self-service password reset tools to gain access to other personal and corporate resources.
The single most important tool to prevent that sort of compromise is multi-factor authentication (MFA). Enterprise Office 365 plans have had that feature since last June for users assigned to administrative roles. Now, that capability is available for any user in Office 365 Midsize Business, Enterprise, Academic, and Nonprofit plans as well as the standalone versions of Exchange Online and SharePoint Online. The change was announced yesterday in a post on the Office blog.
Setting up MFA for users requires a trip to the Office 365 administrative interface with global administrator’s credentials. All of the MFA settings are accessible via a link at the top of the Office 365 Admin interface.
After opening that panel, you can select the users you want to set up and then click Enable.
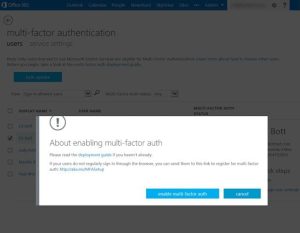
When multi-factor authentication is enabled for a user account, users are required to correctly enter their password and then provide a second form of authentication—a code sent via text message or phone call to a number associated with the account, or one generated by an authenticator app on a smartphone.

The new changes also affect Office 365 desktop apps, which require separate app passwords when MFA is enabled. (If you’ve used MFA with Google apps or Gmail accounts, this should be a familiar scenario.)
In my testing, setting up Office 365 MFA was a straightforward process on both the administrator and user sides. The one glitch I encountered was an inability to configure the Authenticator app on a Windows Phone.
Update: It took too many tries, but I was eventually able to get the mobile app working correctly. It’s worth noting that the Microsoft Authenticator app, which works with Microsoft accounts and other online services, will not work for Office 365. Instead, you need the Windows Azure Multi-Factor Authentication app, which is available for Windows Phone, Android, and IOS.
One big gap in this otherwise well-implemented security feature is that it doesn’t support Office 365 Small Business accounts. The roadmap in the Office blog post doesn’t mention that SKU, and an Office spokesperson declined to comment on whether those plans can expect this feature to be added at some point in the future.