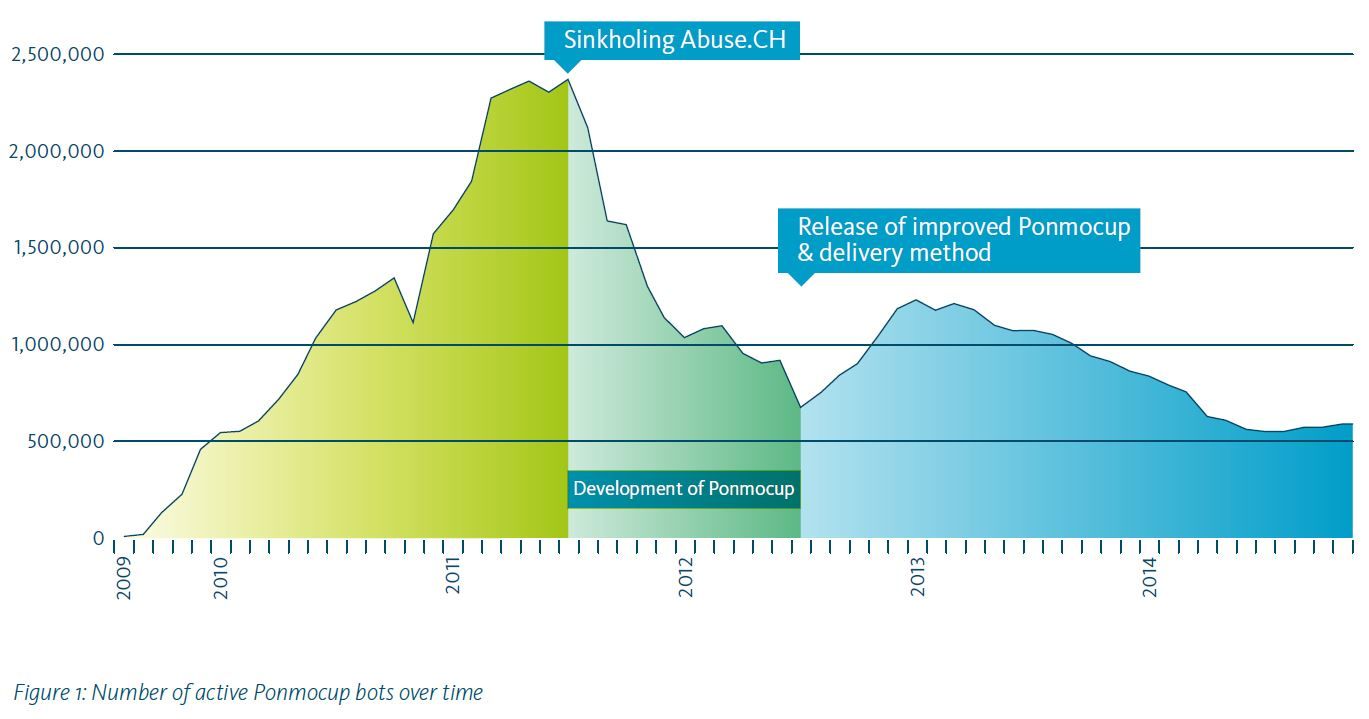
‘Ponmocup’ botnet controlled 2.4 million infections at its peak in 2011 and now holds about half a million machines under its power.
Botconf One of the world’s most successful, oldest, and largest botnets is an underestimated and largely-unknown threat that has over time infected 15 million machines and made millions plundering bank accounts.
The findings from a team of eight Fox IT researchers say the ‘Ponmocup’ botnet controlled 2.4 million infections at its peak in 2011 and now holds about half a million machines under its power.
Lead author Maarten van Dantzig presented the work at the BotConf conference this week in the paperPonmocup: A giant hiding in the shadows [PDF].
In it he and researchers Danny Heppener; Frank Ruiz; Yonathan Klijnsma; Yun Zheng Hu Erik de Jong; Krijn de Mik, and Lennart Haagsma say how the malware first described in 2006 has a strong focus on stealth and has made its likely Russian authors millions of dollars.
“Compared to other botnets, Ponmocup is one of the largest currently active and, with nine consecutive years, also one of the longest running [but it] is rarely noticed as the operators take care to keep it operating under the radar,” van Dantzig says .
“Although it is difficult to quantify the exact amount of money earned with the Ponmocup botnet, it is likely that it has already been a multi-million dollar business for years now.
“Firstly, their infrastructure is complex, distributed and extensive, with servers for dedicated tasks.”
Van Dantzig says the attackers maintain comprehensive infrastructure that is quality tested, and updated to improve robustness stealth, and can quickly mitigate risks.
They are he says technically sophisticated with a deep access of Windows and some 10 years malware development experience.
So far the team has found some 25 unique plug-ins and a whopping 4000 variants that indicate continuous development.
The malware includes anti-analysis tricks such as heuristic checks for network and host-based analysis tools, debuggers and virtualised environments. It also drops clever fake payloads to throw off analysts, the researcher team says.
One of the payloads injects an obvious executable into running processes that serves as an annoying advertising injector commonly found in horrid software bundlers.