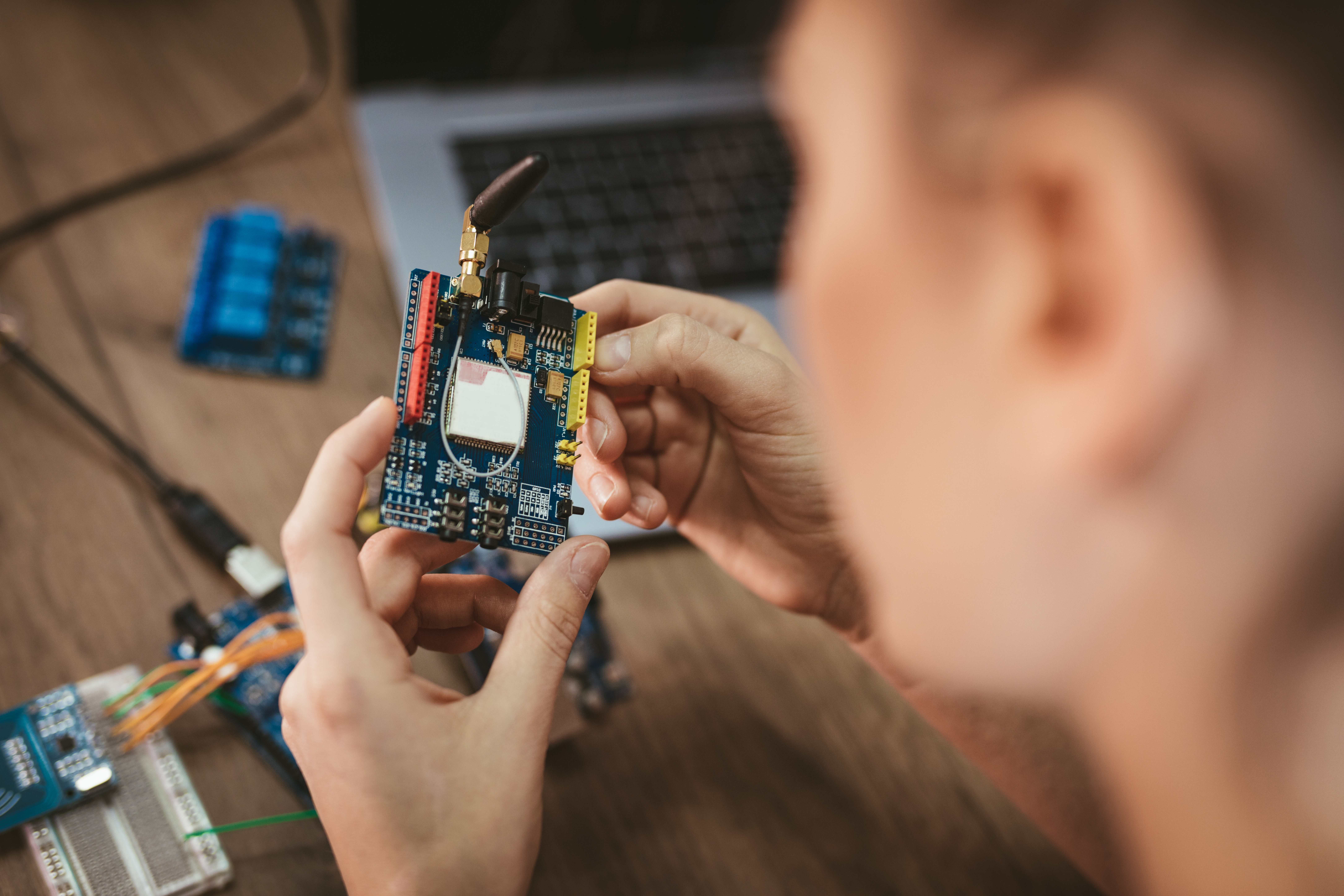
Hands-On Learning
Hack real IoT devices with practical labs and guided challenges — no fluff, just the tools and skills you’ll use in the field.
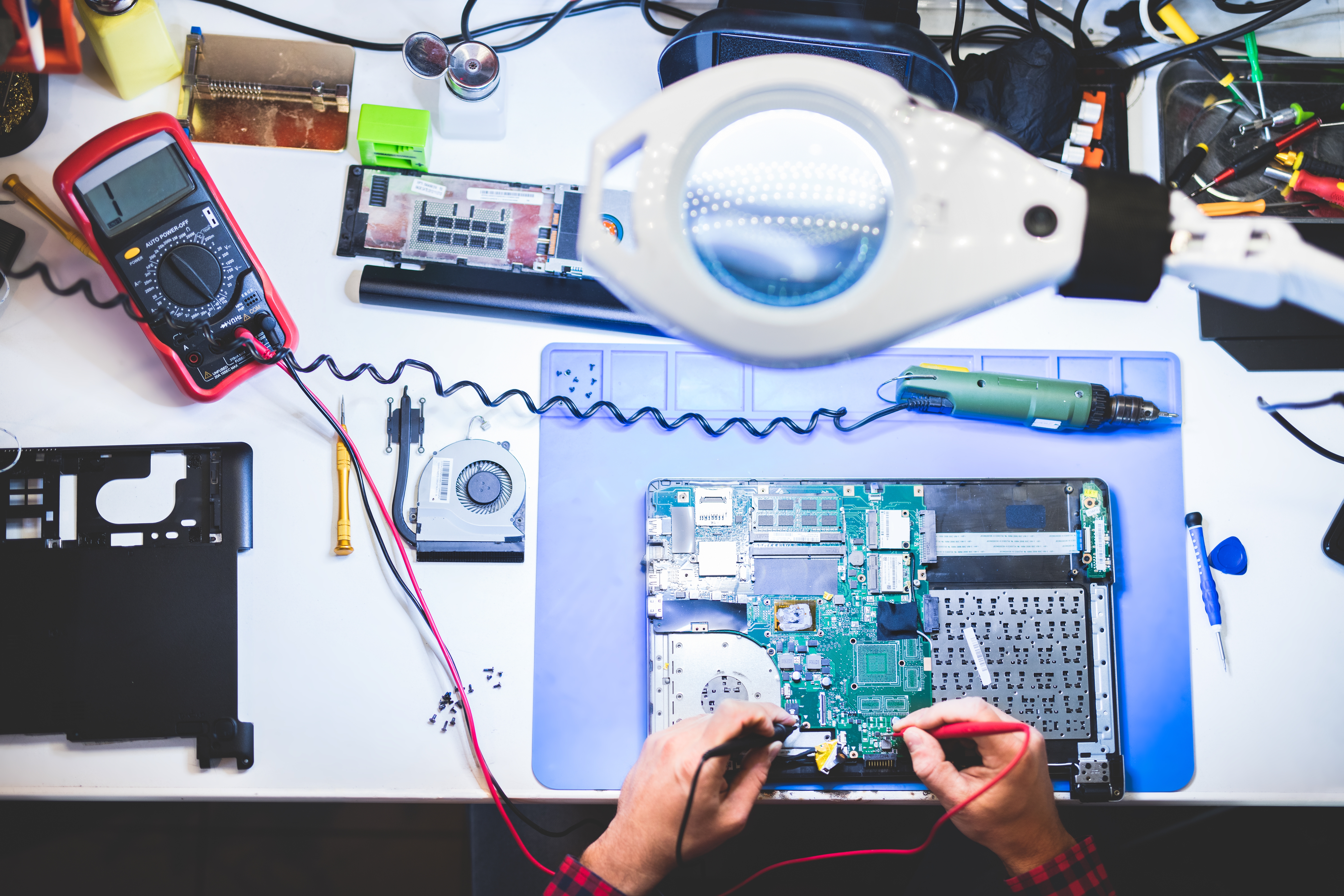
Comprehensive Curriculum
From hardware hacking to firmware reverse engineering, network exploitation, and application flaws — everything you need to master IoT pentesting in one course.
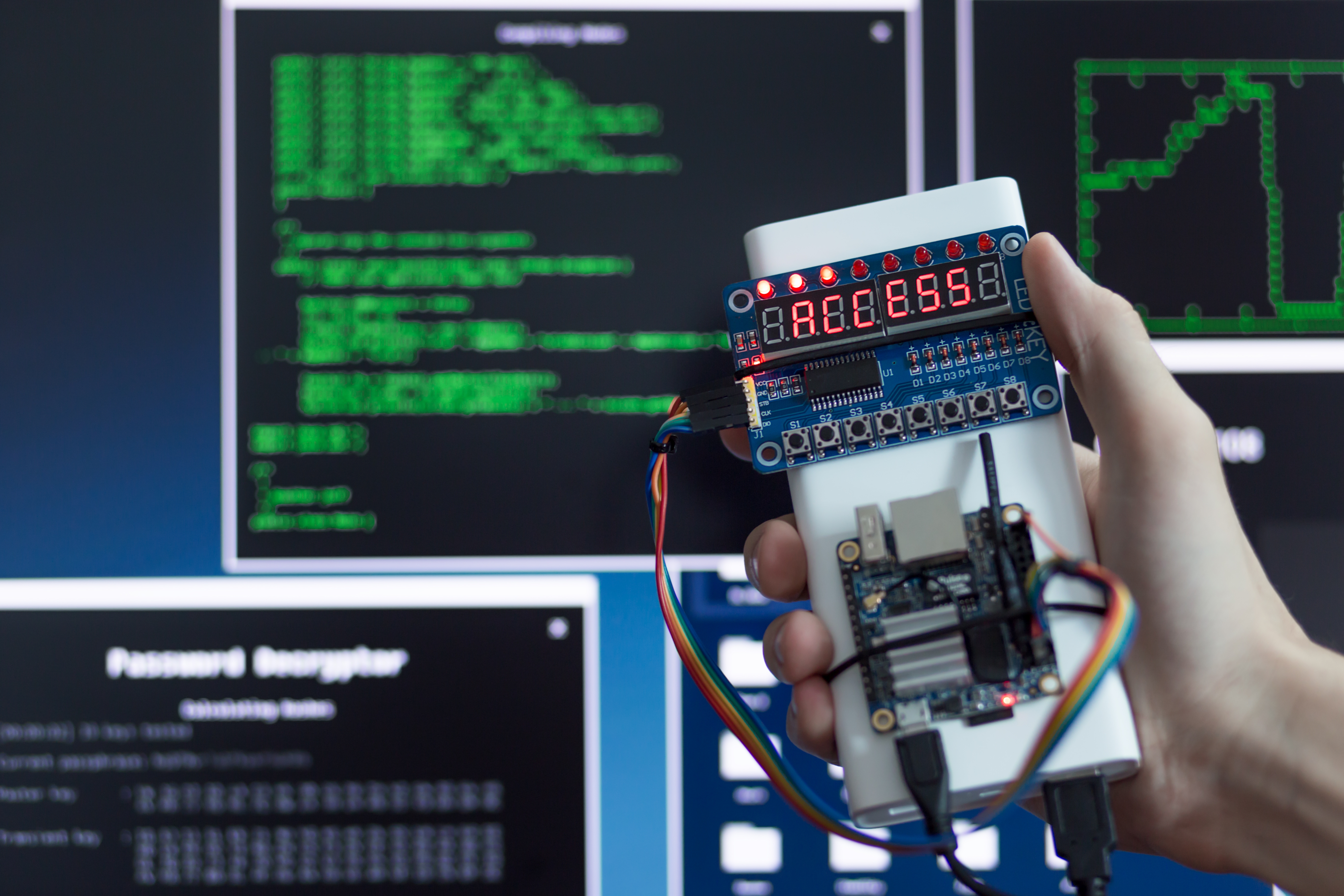
Real-World Scenarios
Apply your skills across industries like automotive, healthcare, manufacturing, and ICS — the same environments targeted by today’s attackers.
About the Course
The IoT Hacking, Pentesting & Exploitation course will take you inside the world of connected devices and show you exactly how attackers and security professionals evaluate them. You’ll learn how to identify weaknesses, build threat models, and apply proven techniques across every layer of the OSI model — from firmware and network protocols to hardware interfaces and application flaws. Through hands-on labs, you’ll gain the practical skills companies are looking for: 🔧 Hardware Hacking & Soldering Basics 🧩 Firmware Extraction & Reverse Engineering 🌐 Network Protocol Analysis 🔐 Exploitation of IoT Devices in Real Scenarios This course goes beyond theory — it gives you the framework, methodology, and mindset to test IoT devices across industries such as automotive, healthcare, manufacturing, and industrial control systems. While the technology differs, the risk model is the same: devices can be hacked, and you’ll know how to do it. By the end, you’ll be equipped to perform professional-level IoT pentests, exploit vulnerabilities responsibly, and help secure the ever-expanding world of connected devices.

About the Creator
Hi, I'm your instructor, [Your Name]. With years of experience in IoT security, I've faced various challenges and conquered them to become an expert in the field. I'm excited to share my knowledge and help you navigate the complex world of IoT security. My goal is to equip you with the skills to excel in evaluating IoT devices and ensuring their security.
Course Curriculum
-
1
Introduction to IoT and Security
-
2
Unit 1: Your Hacking IoT Arsenal
- Hardware & Tools Free preview
- Software & Applications Free preview
-
(Included in full purchase)
BOM & Shopping List Used on this Course
-
3
Unit2: Hardware Hacking
-
(Included in full purchase)
How to Use a Multimeter
-
(Included in full purchase)
FCC and Datasheets are your Friends
-
(Included in full purchase)
Detecting Pinout of UART Interfaces
-
(Included in full purchase)
Detecting Pinout on JTAG Interfaces
-
(Included in full purchase)
Extracting Firmware from SPI Interfaces
-
(Included in full purchase)
Hardware Hacking Challenge
-
(Included in full purchase)
Hardware Challenge Solution
-
(Included in full purchase)
-
4
Unit 3: Firmware Analysis
-
(Included in full purchase)
Introduction to Firmware Analysis
-
(Included in full purchase)
Binwalk and File Systems
-
(Included in full purchase)
Finding Firmware Vulnerabilities
-
(Included in full purchase)
Firmware Analysis Automation
-
(Included in full purchase)
Firmware Hacking Challenge
-
(Included in full purchase)
Firmware Hacking Solution
-
(Included in full purchase)
-
5
Unit 4: Software Defined Radio
-
(Included in full purchase)
Introduction to SDR
-
(Included in full purchase)
Setting Up your SDR Lab
-
(Included in full purchase)
Analyzing Radio Signals
-
(Included in full purchase)
SDR Hacking Challenge
-
(Included in full purchase)
SDR Hacking Solution
-
(Included in full purchase)
-
6
Unit 5: Hacking BLE
-
(Included in full purchase)
Introduction to BLE
-
(Included in full purchase)
Discovering and Interacting with BLE Devices
-
(Included in full purchase)
BLE Hacking Challenge
-
(Included in full purchase)
Ble Challenge Solution
-
(Included in full purchase)
-
7
Unit 6: Hacking Zigbee
-
(Included in full purchase)
Introduction to Zigbee
-
(Included in full purchase)
Setting Up your Zigbee Lab
-
(Included in full purchase)
Analyzing Zigbee Traffic
-
(Included in full purchase)
Zigbee Hacking Challenge
-
(Included in full purchase)
Zigbee Hacking Solution
-
(Included in full purchase)
-
8
Conclusion
-
(Included in full purchase)
Final Conclusion and Next Steps
-
(Included in full purchase)
What People Are Saying
Discover how our course is making a difference for our students
This course was a game-changer for me. I had basic security knowledge, but never touched IoT devices before. The hands-on labs made complex concepts simple, and now I can confidently perform full IoT pentests for my clients.
Oakland, California

I’m preparing for OSCP and wanted more practical IoT experience. This course delivered way more than I expected — especially the step-by-step exploitation exercises. Highly recommend it to anyone who wants to stand out in cybersecurity.
Miami, Florida

As a red teamer, I wanted to expand into IoT hacking. This course gave me exactly what I needed — firmware analysis, hardware exploitation, and real-world methodology. I used what I learned here in my last engagement and found critical device flaws.
Buenos Aires, Argentina
Ready to Master IoT Security?
Enroll now to unlock the tools and techniques needed to evaluate IoT devices with confidence
$299.00
