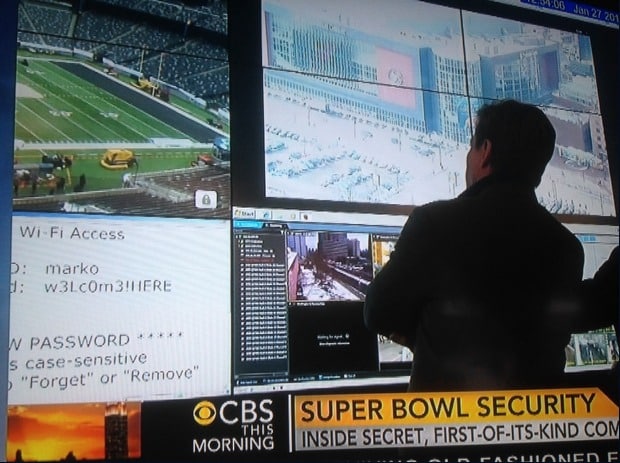
Summary: Prior to the start of Super Bowl 48, the stadium’s internal Wi-Fi login credentials were inadvertently broadcast on national TV.
During the pre-game coverage for NFL Super Bowl XLVIII, television news inadvertently broadcast the stadium’s internal Wi-Fi login credentials, which were in plain sight on an enormous, unmissable, wall-mounted monitor inside a command center.
The Wi-Fi credentials, which have likely been changed as news of the security gaffe has spreadlike wildfire on Twitter and community blogs, had “marko” as the login, and a pseudo-leet speak variation of ‘welcome here’ as the password.
The televised segment broadcast this morning was a feature that gave a first-time peek into Super Bowl security headquarters.
It would appear that network security at the MetLife Stadium in East Rutherford, New Jersey, is not up to enterprise levels.

According to Mobile Sports Report, the in-stadium Wi-Fi network at MetLife Stadium, built by Verizon, is free and open to customers of all carriers.
The credentials accidentally broadcast on TV may likely be an internal set of Wi-Fi access credentials, possibly for staff, press or ticketing systems.
While it’s good to see the stadium’s credentials were not ‘admin’ and ‘password’ the security failure will no doubt become yet another example of what not to do.
This year’s Super Bowl match, where the Seattle Seahawks face off to the Denver Broncos, is expecting over 82,000 Wi-Fi-enabled guests this year.
Last year Ars Technica reported that along with a “no outside food” policy, attendees were disallowed from bringing wireless equipment that might interfere with the New Orleans Mercedes-Benz Superdome’s Wi-Fi network.
“The NFL has a very robust frequency coordination solution in place,” Dave Stewart, director of IT and production for Superdome management firm SMG, told me in a phone interview. “Every device that enters the building has to go through a frequency scan and be authorized to enter.At the perimeter the devices are identified and tagged. If they present a potential for interference, they are remediated at that moment. Either the channel is changed or it is denied access. It’s all stopped at the perimeter for this event.”In Stewart’s words, the goal is to prevent any “rogue access points or rogue equipment from attempting to operate in the same frequency” as the stadium Wi-Fi network (“rogue” as in “not under the control of the system administrators”).
The system went down during the game due to a “relay failure.”
Hopefully after today’s gaffe, Super Bowl security standards within the organization will be encouraged to meet the level of those as robust as those exercised on fans.